Table of Contents
Introduction

Keyloggers and How to Protect Against It – A keylogger is a type of malware that records every keystroke you make on your computer or mobile device. Insert your passwords, credit card numbers, and any other sensitive information you type. Keyloggers can use to steal your identity, commit fraud, or blackmail you.
What is a keylogger?
A keylogger is a kind of malware that histories every keystroke you make on your computer or mobile device. Consist of your passwords, credit card numbers, and any other sensitive information you type. Keyloggers can install on your computer or mobile device without your knowledge and can be very difficult to detect.
How does a keylogger work?
Keyloggers work by recording the input from your keyboard. This input is then saved to a file on your computer or mobile device. The keylogger can send this file to the attacker, who can view it and steal your sensitive information.
How to detect a keylogger
There are a few ways to detect a keylogger on your computer or mobile device. One way is to use a keylogger detection tool. These tools scan your computer or mobile device for keyloggers and alert you if they find one. Another way to detect a keylogger is to look for the following signs:
- Your computer or mobile device is running slower than usual.
- You see strange pop-up ads or messages.
- Your passwords or credit card numbers are present stolen.
- You see unskilled programs running in the background.
If you suspect you may have a keylogger on your computer or mobile device, it is essential to take action immediately. You should:
- Run a keylogger detection tool.
- Change your passwords and credit card numbers.
- Scan your computer or mobile device for malware.
- Report the keylogger to the authorities.
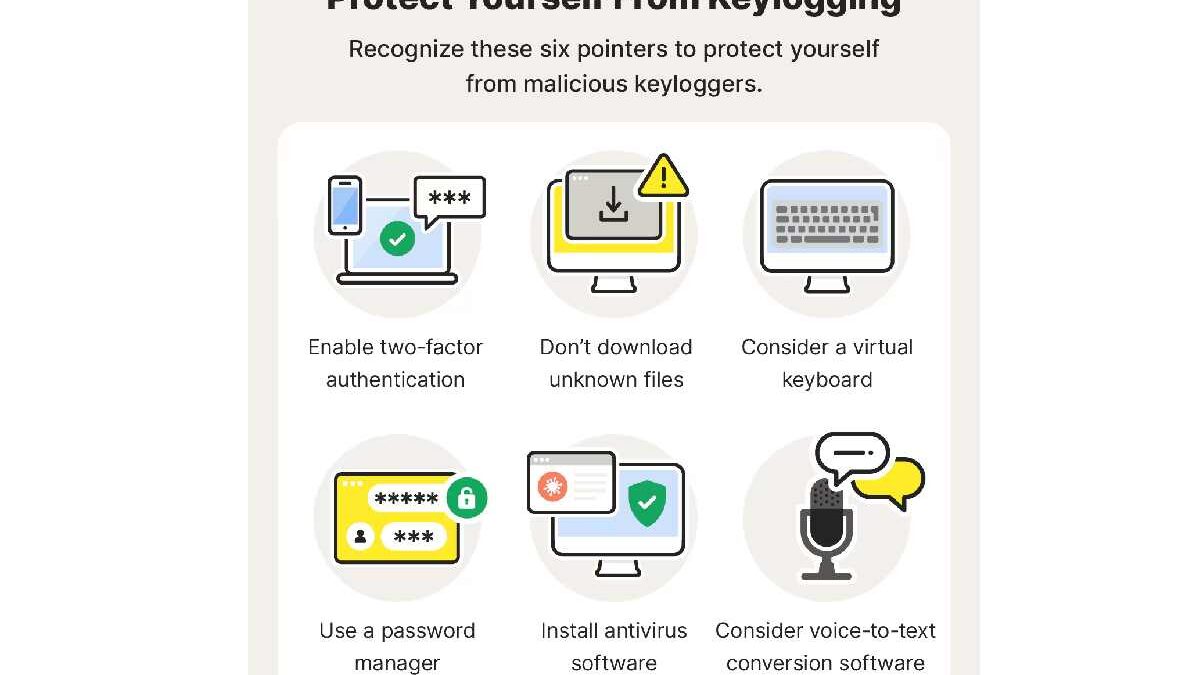
How to protect yourself from keyloggers
There are a few things you can do to protect yourself from keyloggers:
- Use a firewall and antivirus software.
- Keep your software up to date.
- Be careful about what sites you visit and what files you download.
- Use a strong password manager.
- Avoid using public computers for sensitive tasks.
By following these tips, you can help to protect yourself from keyloggers and other types of malware.
Keyloggers and How to Protect Against It
Keyloggers are malicious software or pieces of hardware that monitor and record your keystrokes as you type.
With the use of a command-and-control (C&C) server, it takes the data and transfers it to a hacker.
The hacker utilizes the usernames and passwords they find by analyzing the keystrokes to access otherwise secure systems.
Types of Keyloggers
- A type of malware called a software keylogger infects your device and, if intended, can spread to other gadgets the computer comes into touch with.
- A hardware keylogger communicates information to the hacker or hacking group.
- Which they will use to infiltrate your computer, network, or anything else that needs authentication to access it, unlike a software keylogger, which can spread from one device to another.
4 Ways to Protect Yourself Against Keyloggers
One of the most dreaded threats to computer security is keyloggers. Follow these suggestions to avoid being a hacker’s target.
One of the most well-known and dreaded computer security concerns today is keyloggers. Keyloggers have a terrible reputation for several reasons, including that they are difficult to detect and can directly harm you beyond the computer and screen in front of you.
Keylogger security covers a very typical security spectrum. You require this level of protection daily for your personal and online digital security. Keyloggers are simply one type of security measure available.
1. Use a Firewall
- In most cases, the keylogger must send its data back to the attacker to be harmful. Data must be transmitted from your computer by the keylogger over the internet.
- There’s a risk that a firewall, like Windows Firewall, the default security configuration for Windows 10 systems.
- Will notice something isn’t quite right as your internet traffic travels through it.
2. Install a Password Manager
- Updating and switching your passwords is a regular security tip (along with using a solid single-use password, to begin with).
But let’s face it: with the significant number of websites that most of us use, it’s challenging to remember tens of 16-character passwords.
- Keyloggers are efficient because they are so straightforward—copy keystrokes and log the data.
3. Update Your System (And Keep It That Way)
- Always be proactive when it comes to system security. Keeping your system updated is one of the most crucial aspects of proactive protection.
- That encompasses both your operating system and the software and applications you use with it.
- Keyloggers and another malware search for vulnerabilities in out-of-date software and can exploit them, sometimes without your knowledge.
4. Consider Additional Security Tools
- Although Windows 10 and macOS’s default security settings are adequate, you should always consider beefing them up for the best possible security.
- Check out our selection of your computer’s top antivirus and security programs.
- Although several of these have macOS equivalents, they are Windows-focused and well worth the tiny investment.